System Architecture
(INFT12-212 and 72-212)
Lab Notes for Week 11: File Systems, File System Calls
1 Features of Files
1.1 File Names
Unix files have one or more names. Names can consist of the characters
A-Z, a-z, 0-9 and most punctuation. Spaces are not allowed; neither
is the '/' character (why not)?
Files are organised hierarchically into directories, mainly
for the benefit of the users. There are two ways of expressing the
name of each file:
1.2 Activity
Imagine that you are user mary, and when you log in your
working directory is /home/student/mary. Your home directory
looks like:
drwxr-xr-x 2 mary student 512 Apr 24 14:41 Mail
-rw------- 1 mary student 423 Apr 20 12:20 diary
-rw-r--r-- 1 mary student 25931 Apr 20 15:50 notes
-rw-rw-r-- 1 mary student 201486 Apr 20 15:50 things_todo
What are the relative and absolute names for these four files/directories?
If you now cd into the Mail directory, you find
the files:
-r-------- 1 mary student 4387 Apr 11 11:20 Andrea
-rw-r----- 1 mary student 161 Apr 11 11:02 Bill
-rw-r----- 1 mary student 401 Apr 17 13:00 Karen
-rw-r----- 1 mary student 2324 Apr 17 12:59 Loren
-rwxr-x--- 1 mary student 132412 Apr 17 12:59 Mick
-rw-r----- 1 mary student 1641 Apr 11 11:56 Steven
-rw-r----- 1 mary student 4528 Apr 17 12:54 Vicki
Give an absolute and relative way of viewing the file Andrea?
Hint: the less command allows you to view files. Do the same
for the file things_todo, without moving out of
the Mail directory.
If another student, kim, has a file called for_mary
in her home area, how can you view the file with the less
program?
1.3 File Metadata
Every operating system keeps information about files: their name,
their size, etc. This is known as file metadata. The metadata
that Unix keeps on each file is given below (with the Unix name for
each piece of data):
- st_dev
- The device number of the device containing the i-node.
This tells you on what device the file is stored.
- st_ino
- The i-node number. Each file has a unique i-node number
(that is, unique on that particular device).
- st_mode
- The 16-bit protection for the file. See below.
- st_nlink
- The number of name links to this file.
- st_uid
- The user-ID of the file's owner.
- st_gid
- The group-ID; this and the protection affects how certain
people can use the file.
- st_size
- The current size of the file.
- st_atime
- The access time as the number of seconds since 1970.
Updated whenever the file is read, but not when a directory that appears
in a path is searched.
- st_mtime
- The modification time, updated when the file is written.
Updated when a link is added to or removed from a directory.
- st_ctime
- The status-change time, updated when the file is written
or when the mode, owner, group, link count, or modification time is
changed.
The protection entry is broken into several fields:
| File Type | Set-uid | User | Group | Other |
| 4 bits | sgt | rwx | rwx | rwx |
Let's tackle the right-most three fields first. Each gives read, write
and execute permissions to a particular user. Each user in Unix has
a unique it user-ID and one or more group-IDs. A user can
access a file if:
- The file is owned by the user, and the appropriate User permission
is on, else
- The file's group-ID matches one of the group-IDs that the user has,
and the appropriate Group permission is on, else
- The appropriate Other permission is on.
The read, write and execute permissions allow you to read and write
to files and directories, and to execute (i.e run) a program if it
is stored in a file. However, you can't execute a directory, so what
does the execute permission mean here? If a directory has execute
permissions, then it can be searched, for example by an ls
command.
Let's have a look at some examples. Try the id command to
see what user-ID and group-IDs you have:
$ id
uid=5125(fred) gid=100(student)
This gives your numeric user- and group-IDs, with the textual names
in parentheses. Imagine that you are user-ID mary, with group
IDs student and masters. Which files can you read
and write to below? Which directories can you look in?
drwx------ 4 mary student 1024 Aug 15 1995 TeX
drwx------ 9 mary masters 512 Jan 5 1996 Units
drwxr-x--- 3 fred student 512 Jun 18 1996 Wish
drwxr-x--- 2 mary staff 512 Apr 17 12:54 code_tools
-rw-rw---- 1 mary student 141 Apr 3 18:12 diskit
-rw-r----- 1 mary student 140 Apr 3 18:14 forkit.c
drwxr-xr-x 26 joe admin 1024 Mar 5 08:19 inferno
----r----- 1 mary student 39 Apr 3 18:22 stopit
-------rwx 1 mary student 6452 Apr 17 18:22 thrash
-r--rw---- 1 mary student 807 Apr 17 18:22 thrash.c
-rw-r----- 1 jim masters 22 Apr 3 18:06 while.c
Mary's file thrash has very strange permissions. Explain
them.
We will leave the Setuid permission fields until the security lab.
The left-most field in the protection data is the type of file. Unix
has the following file types:
- REG (-)
- A regular file.
- DIR (d)
- A directory.
- CHR (c)
- A character device (used for direct device access).
- BLK (b)
- A block device (used for direct device access).
- LNK (l)
- A symbolic link (more later).
- FIFO (f)
- A named pipe.
- SOCK (s)
- A socket.
1.4 Activity
Download the file stat.c into your home area
and compile it as per usual.
Now use stat to look at the metadata of files in your home
area, e.g ./stat stat.c. Compare the results from stat
with ls -l. Look at some directories with stat as
well. Make some directories with mkdir if you don't have
any.
1.5 Holey Files
We talked about `holey files' in the OS lectures. Let's create a holey
file and see what one looks like.
Download the file lseek.c into your home
area and compile it as per usual.
This program creates and opens a new file, seeks a million characters
from the beginning, and writes the words `The end' there, then closes
the file. How big should the file be? Do an ls -l on the
created file and see how big it really is. Now run the program du
-a which show how many 1K disk blocks each files actually takes up.
You should see a considerable difference in the size in bytes, and
the size in disk blocks. Once you've finished this section, remove
the holey file; if you don't, it will take up a lot of space on our
backups!
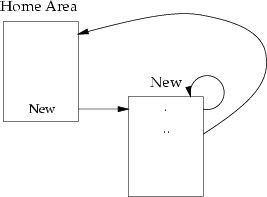
1.6 Directory Links
The number of links a file has indicates the number of names that
the file has; remember that Unix allows a file to have multiple names.
As directories are also files, they too can have any number of names.
Create a new directory called New in your home area. Do an
ls -l in your home area. How many links does the New
directory have? Can you explain this?
Hint: Consider the following picture showing the created name links:
1.7 Security - Changing File Permissions
We looked at file permissions in the last lab. The command used to
change file permissions in Unix is chmod, and is used as
follows:
$ chmod [ugo][+-=][rwx] file [file ...]
where you can choose one or more letters from the ugo list,
exactly one letter from the +-= list and one or more letters
from the rwx list. You can also name more than one file on
the command line.
ugo sets the permissions columns which are affected, rwx
sets the particular permissions, and +- enables or disables
permissions. The = operation turns on the permissions named,
and turns off all other permissions.
1.8 Activity
Explain what the following chmod commands do:
$ chmod ug+r file
$ chmod ugo+rx directory
$ chmod go=rx directory
$ chmod go-w file1 file2 file3
$ chmod u-w file
$ chmod go-rx directory1 directory2
Do an ls -la directory listing of your home directory and
subdirectories. Use chmod to set the appropriate permissions
on your files or directories.
1.9 The Sticky Bit Permission Flag
If you are user mary and you had the following directory
in your home area:
drwxrwxrwx 12 mary student 512 Jan 13 14:19 Share_area
explain what things other users could do in the directory. If there
is a file called my_file owned by mary in Share_area,
can other users rename it? Can other users alter the file's contents?
Can other users delete the file?
In order to reduce problems on shared-writeable directories, modern
versions of Unix have a permission flag called the `sticky bit'. This
can be set using chmod, and the permission flag is shown by ls
as follows:
$ ls -ld Share_area
drwxrwxrwx 12 mary student 512 Jan 13 14:19 Share_area
$ chmod u+t Share_area
$ ls -ld Share_area
drwxrwxrwt 12 mary student 512 Jan 13 14:19 Share_area
When the `sticky bit' is set, only the owner of a file can make changes
to the file's metadata. This allows the file's contents to be shared
(with appropriate access permissions), but prevents other people from
renaming or deleting the file itself.
1.10 Activity
The two main temporary directories in Unix, /tmp and /usr/tmp,
have their `sticky bit' turned on:
$ ls -ld /tmp /usr/tmp
drwxrwxrwt 9 sys sys 2941 May 27 11:05 /tmp
drwxrwxrwt 75 sys sys 9216 May 27 11:07 /usr/tmp
Cd into the /tmp directory and see if you can rename or delete
files owned by other people in these directories. Note that Linux
doesn't have the /usr/tmp directory.
1.11 Set-User Permission Flags
Often you have a file that you want to give users permission to work
on, but the normal Unix permissions are not enough. For example, users
need to change their password, which is stored in /etc/shadow.
But if we let all users write into /etc/shadow, then they
could change other users' passwords!
Unix overcomes this problem by marking programs with a special flag.
For example, on systems not using LDAP, the program passwd
is used to change your password; it must be able to modify the /etc/shadow
file, but only for your password.
$ ls -l /etc/shadow /bin/passwd
-rw------- 1 root sys 772 Jun 14 13:17 /etc/shadow
-r-sr-xr-x 3 root sys 99640 Oct 6 1998 /bin/passwd
As you can see above, the execute (`x') permission on the program
is now an `s'. This means the programs is a set-user program.
When a set-user program runs, it runs with the identity of
the program's owner, and not the person running the program.
If you run /bin/passwd, it runs with root identity,
and not your identity.
So when you run /bin/passwd, it runs as user root,
and root can edit the file /etc/shadow.
1.12 Activity
Do a long listing of the files /home/staff/wkt/suid and /home/staff/wkt/suid2.
You should see that they are identical, but suid2 has the
set-user permission turned on.
The suid and suid2 programs, when run, show you
the contents of wkt's home directory, and try to show you
the contents of the directory hidden_directory which is
in wkt's home directory.
Explain why, when you run /home/staff/wkt/suid, you cannot
see what is in the hidden_directory? What is stopping you
from seeing in there? Can you run a command other than suid
to see in there?
Now run /home/staff/wkt/suid2. Explain why this program can
see what is in the hidden_directory? What allows it to see
in there? Can you run a command other than suid2 to see in
there?
If you enable the set-user permission on a program that you wrote,
what security implications does this have? Do you think you should
leave your set-user programs lying around on the system where anybody
can run them?
Why would it not be advisable to do the command rm * as
the last line in the program?
1.13 Activity
The following command lists all of the set-user programs on the system:
$ find / -perm -04000 -exec ls -l {} \; 2> /dev/null
(It can take quite a while to run). Who owns most of the programs?
What effective user-ID is used when most of these programs are run?
Explain why these programs have have the set-user bit turned on?
Explain why none of these programs should be writeable by group or
others? Alternatively, explain what problems could occur if they were
writeable by group or others?
2 File-related System Calls
The main four Unix and Linux systems calls related to files are:
- open(),
open a file for reading, writing, or both
- close(),
close an open file
- read(),
read some data from a file
- write(),
write some data to a file
Here is an example C program which opens
two files, one for reading and the other for writing, and copies the
contents of the first file into the second. Compile and run it as
per usual.
3 Outlook for the Next Lab
In the last lab, we will look at threads and thread scheduling.
File translated from
TEX
by
TTH,
version 3.85.
On 13 Jan 2012, 11:27.

